NTLMV2和Response消息生成步骤如下: 1.将大写的User name与Domain name区分大小写拼接在一起进行十六进制转换, 然后双字节Unicode编码得到data,接着使用16B NTLM哈希值作为密钥key, 用data 和key进行HMAC-MD5加密得到NTLM v2 Hash。 2.构建一个blob信息。 3.使用16字节NTLM v2 Hash作为密钥,将HMAC-MD5消息认证代码算法加密一个值 (来自Type2的Challenge与blob拼接在一起),得到一个16BNTProofStr(HMAC-MD5). 4.将NTProofStr与blob拼接起来得到Response,使用Responder工具抓取 NTLM Response消息的时候抓取的都是Net-NTLM Hash格式的数据。 Net-NTLM v2 Hash格式如下: username:domain:challenge:HMAC-MD5:blob
所以我们可以依次找到username,domain,challenge,HMAC-MD5,blob
1.在Wireshark中打开包含NTLMv2散列的.pcap文件。
2.找到身份验证的握手包

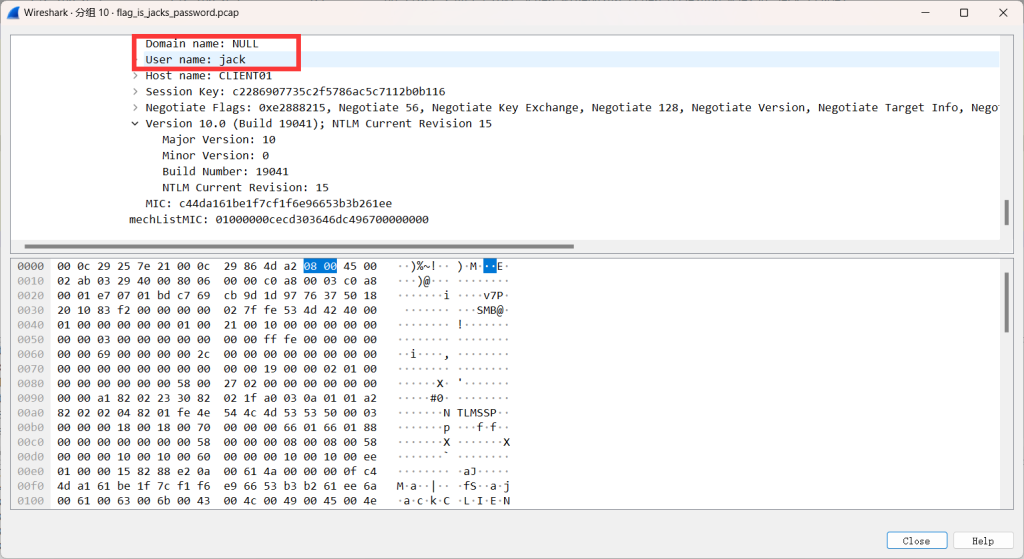
得到username:jack
domain:null
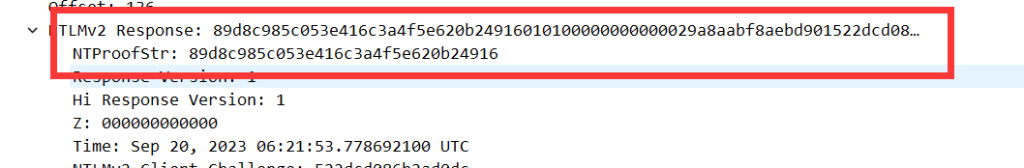
上面为blob下面为hash89d8c985c053e416c3a4f5e620b24916010100000000000029a8aabf8aebd901522dcd086b2ad0dc00000000020012005700490044004700450054004c004c004300010008004400430030003100040024005700690064006700650074004c004c0043002e0049006e007400650072006e0061006c0003002e0044004300300031002e005700690064006700650074004c004c0043002e0049006e007400650072006e0061006c00050024005700690064006700650074004c004c0043002e0049006e007400650072006e0061006c000700080029a8aabf8aebd901060004000200000008003000300000000000000000000000003000003a88f01cc5606f27921bebc4bdbf6ab63d0624ed6d24126f531ff9417f2639b20a0010000000000000000000000000000000000009002e0063006900660073002f005700690064006700650074004c004c0043002e0049006e007400650072006e0061006c000000000000000000
blob中包含了hash要去掉010100000000000029a8aabf8aebd901522dcd086b2ad0dc00000000020012005700490044004700450054004c004c004300010008004400430030003100040024005700690064006700650074004c004c0043002e0049006e007400650072006e0061006c0003002e0044004300300031002e005700690064006700650074004c004c0043002e0049006e007400650072006e0061006c00050024005700690064006700650074004c004c0043002e0049006e007400650072006e0061006c000700080029a8aabf8aebd901060004000200000008003000300000000000000000000000003000003a88f01cc5606f27921bebc4bdbf6ab63d0624ed6d24126f531ff9417f2639b20a0010000000000000000000000000000000000009002e0063006900660073002f005700690064006700650074004c004c0043002e0049006e007400650072006e0061006c000000000000000000
在下面这个流量中找到challenge的值
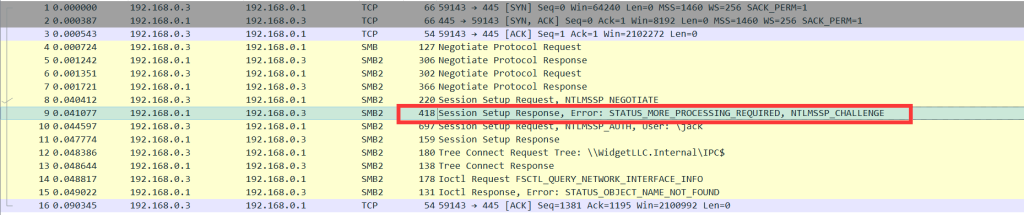
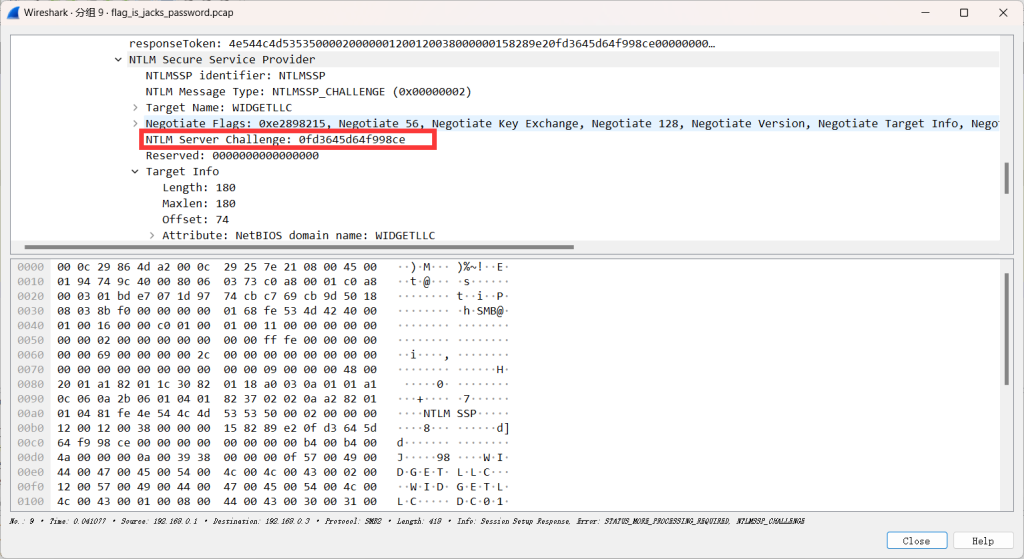
challenge:0fd3645d64f998ce
然后按照格式用txt保存下来
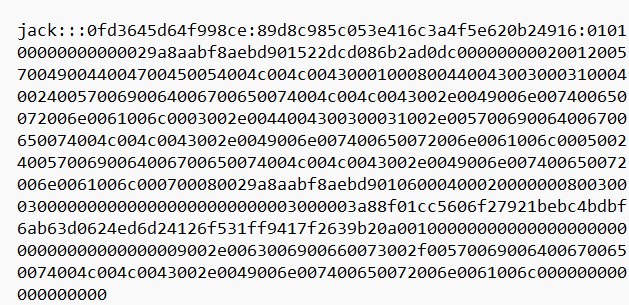
命名为crackme.txt
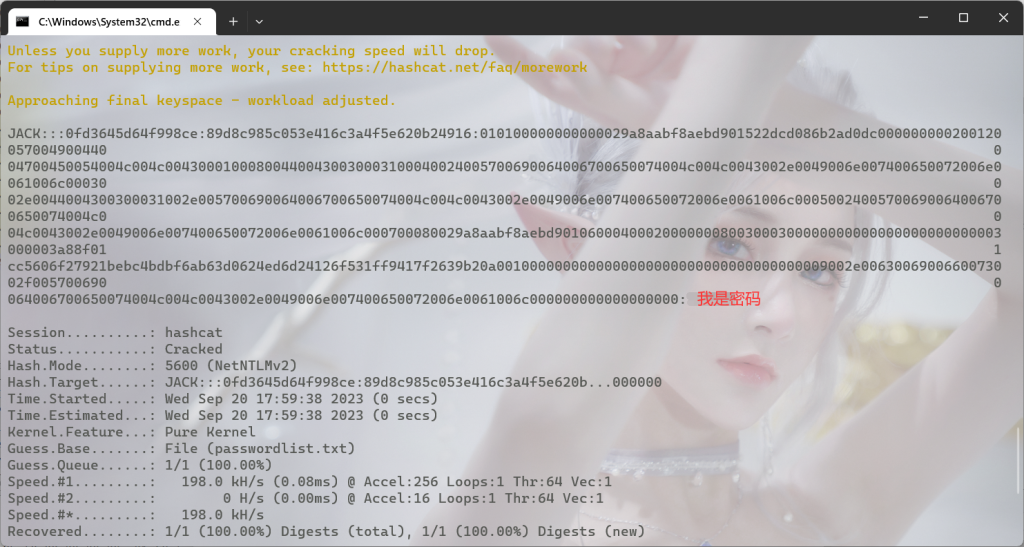
然后找个字典用hashcat爆破
hashcat -m 5600 crackme.txt passwordlist.txt
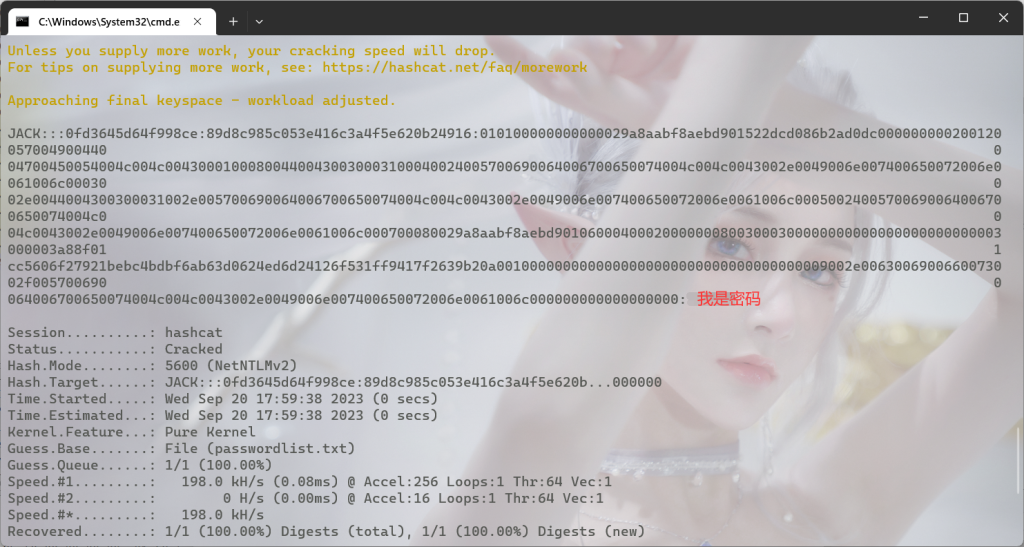
得到密码